The Forrester Wave™: Cybersecurity Risk Ratings Platforms, Q2 2024
Cyber Threat Intelligence Update: New Claims of Attacks Against Israeli SCADA Systems
Executive Summary
- SecurityScorecard’s ongoing collections from hacktivist channels involved in cyber activity provoked by the conflict in Gaza highlight the international scope of the conflict, with hacktivist groups in Indonesia and Malaysia claiming attacks against organizations in Israel and allied states.
- As in the other channels SecurityScorecard analyzed previously, these newly-added channels mainly discuss relatively low-sophistication and low-impact activity.
- Some groups’ claims of access to Israeli water utilities’ Supervisory Control and Data Acquisition (SCADA) systems may provoke more concern than other claims, given the possibility of real-world impact.
- SecurityScorecard’s investigation does not offer clear evidence supporting these claims, but may illustrate threat actors’ ongoing interest in the Israeli water and wastewater systems sector.
Background
SecurityScorecard’s ongoing collections from hacktivist channels involved in cyber activity provoked by the conflict in Gaza continue to reflect the international scope of the conflict. Our recent collections highlight the expansion of hacktivist activity in Indonesia and Malaysia, with a variety of groups declaring their support of the Palestinian cause on the basis of religious solidarity.

Like the other hacktivist groups involved in the conflict, relatively low-sophistication and low-impact activity figures prominently in these channels; claims of responsibility for DDoS attacks, website defacements, and the circulation of purportedly stolen data appear regularly. These have targeted both Israeli organizations and organizations in states supporting Israel.
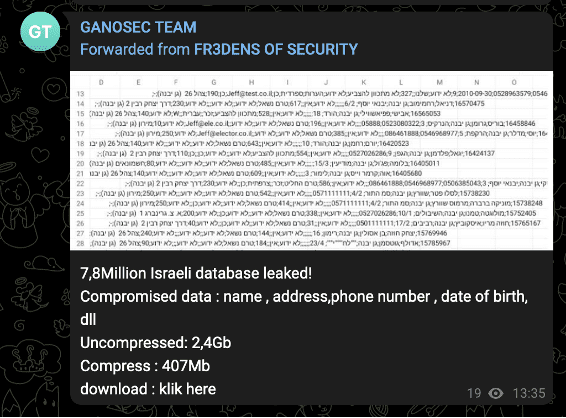
While many of these claims have resembled those circulating in other pro-Palestinian hacktivist channels — with claims of relatively low-impact and low-sophistication appearing frequently — some groups have, however, claimed access to Israeli water treatment organizations’ SCADA systems. If true, this could have a more serious impact than the aforementioned activity.
Findings: SCADA Claims
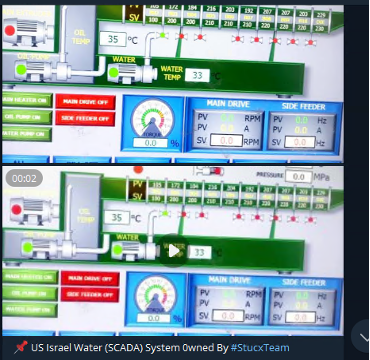
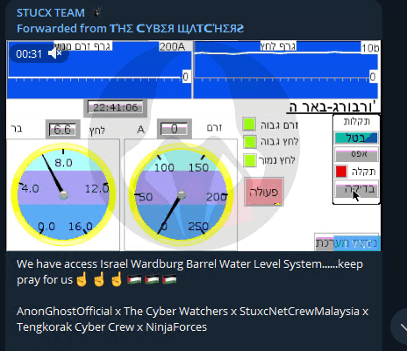
In response to these claims, SecurityScorecard consulted a strategic partner’s NetFlow data to analyze the traffic involving a sample population of Israeli water utility-attributed IP addresses within the period of the claimed attacks (October 19-26). While this data cannot confirm the threat actors’ claims, it may illustrate in greater detail threat actors’ interest in Israel’s critical infrastructure organizations.
In a sample featuring a total of 402,354 individual flows to and from 36 IP addresses SecurityScorecard attributes to the Israeli water and wastewater systems sector, 5,670 flows involved IP addresses linked to anonymizing services including virtual private networks (VPNs), other proxy software, and the onion router (TOR). Threat actors often use such services to conceal the origins of their traffic when communicating with target networks. Flows involving the IP addresses analyzed may therefore represent malicious or suspicious activity.
IP addresses involved in repeated communication with water system-attributed IP addresses may be particularly worthy of note, as repeated communication or longer sessions may reflect persistent access by threat actors. The IP addresses involved in those communications, which may be particularly likely to reflect malicious activity, are available upon request.
This traffic data does not, however, offer clear evidence of the compromise claimed in the screenshots above, and SecurityScorecard’s internal data does not suggest that the Israeli organizations involved faced particularly elevated risks (though, of course, it bears noting that, technical data aside, these organizations may faced more pronounced risks than others simply by virtue of being in critical infrastructure sectors in a country involved in a major conflict).
SecurityScorecard’s scan data does not indicate that the organizations involved have exposed ICS or SCADA services on their network. This may indicate that these services are only accessible through a firewall, given that its scans do reflect the use of firewalls at port 443 of some of the IP addresses in the sample population. This might suggest adherence to guidance (similar to SecurityScorecard’s recommendations) regarding the use of ICS or SCADA devices. Although SecurityScorecard’s new exposed credential collections do contain one record for a login at one of the organization’s subdomains, the username is an @gmail.com email address, which may suggest that the credentials correspond to a customer account or provide access to an otherwise external-facing resource. If that is the case, assuming that the organization’s permissions are sufficiently well-managed (and that external users’ credentials would not yield access to internal systems), the record may be less likely to yield access to a SCADA system.
Conclusion
The available NetFlow data may not indicate that threat actors successfully accessed SCADA services for Israeli water systems within the period in which claims of such access circulated in pro-Palestinian hacktivsts’ Telegram channels. However, the traffic involving IP addresses linked to services used by threat actors for anonymization or obfuscation may suggest reconnaissance or otherwise speak to threat actors’ interest in these organizations without indicating compromise.
